A VPN is one of the most basic techniques to secure your online privacy. The best part is that downloading and utilizing a VPN software is simple. If you’re working from home due to COVID-19 or utilizing insecure Wi-Fi at a coffee shop, here’s how to do it securely!
It may appear alarmist to recommend that you use a virtual private network (VPN) as much as possible, but there are actual dangers to your privacy. Every time you connect to the internet, your internet service provider (ISP) has access to everything you transmit and has been given permission by Congress to sell your anonymised data to advertising.
If Coronavirus has caused you to use public Wi-Fi, unscrupulous people may try to intercept your online traffic. Advertisers may follow your travels across websites and determine your location by looking at your IP address on the open internet. Also, keep in mind what three-letter federal agency may be up to an it’s terrible world out there!
The internet was designed for simple information interchange, not for user privacy, anonymity, or encrypted communication. While HTTPS goes a long way toward securing your data, it does not protect you from all threats. Until and unless a new, more private internet emerges, utilizing a VPN is the simplest approach to ensure that you’re exchanging as little information as possible.
Table of Contents
What a VPN Can and Cannot Do?
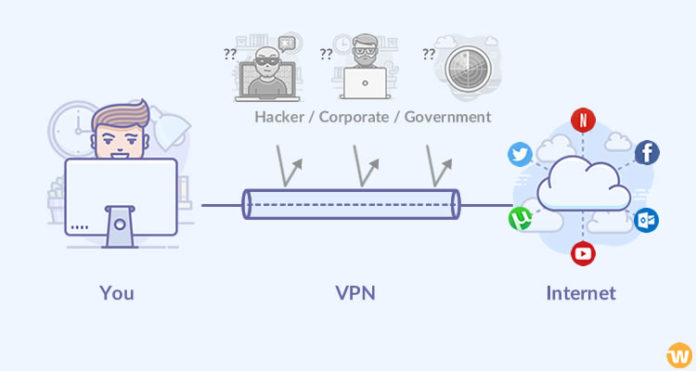
As with any security tool, it’s critical to recognize a VPN’s restrictions. Users would still not anticipate a Kevlar vest to protect you from a parachute, or a parachute would stop a bullet. When you connect to a VPN, your traffic is sent over an encrypted tunnel to a VPN company’s server. This implies that neither your ISP nor anything (or anybody) connected to your router will be able to observe your online traffic.
Your data is sent from the VPN server to the open network. Your true IP address is successfully disguised since your traffic looks to originate from the VPN’s server. This is significant since IP addresses are geographically scattered and may be used to approximate your location. This is useful if you want to fake your location. By connecting to a VPN server in London, you may seem to be browsing the internet from the United Kingdom.
A VPN will not entirely anonymize your traffic. You should utilize the free Tor anonymization network for this. Instead of routing your data through a single intermediary (such as a VPN server), Tor routes it across a network of volunteer computers. This makes it much more difficult for someone trying to follow your actions to know what you’re up to, but keep in mind that it will also slow down your online traffic.
Websites can also track your movements via cookies, browser fingerprinting, internet trackers, and other nefarious methods. Using an ad-blocker like Privacy Badger and a privacy-friendly browser like Firefox will help suppress these ever-watchful pests and make it much more difficult for marketers to track your travels over the web.
It’s vital to realize that when you connect to a VPN, the VPN now has as much information about your online activities as your ISP. Your data should never be sold by a reliable VPN. Instead, it should go to considerable measures to keep as little information about you and your actions as possible. These privacy safeguards should be explicitly specified in the company’s privacy policy.
Our ratings also detail VPNs’ attempts to preserve your privacy. If you’re not happy with the VPN you’re using, consider switching to one you can rely on.
Finally, just because you have a VPN doesn’t imply you should ignore fundamental security precautions. While some VPN services claim to be able to stop malware, we recommend that you install independent antivirus software on your computer because these tools are particularly intended to safeguard your computer from harmful software.
Recycled passwords are a key point of failure, you can protect yourself from password leaks by utilizing a password manager. Dashlane and Keeper are two of our favorite password managers. While you’re securing your passwords, turn on two-factor authentication wherever possible.
Why does your company require a VPN?
VPNs, at its most basic, protect organizations and consumers as well as their private data. Here are some more reasons why your company can profit from a VPN:
Convenience
VPNs are a simple method to provide employees, even remote workers, with easy access to your corporate network without requiring them to be physically present—all while protecting private networks and business resources.
Enhanced security
When compared to other ways of remote communication, communicating over a VPN connection gives a better level of security by keeping private networks closed to persons who do not have authorized access. Users’ real geographic whereabouts are secured and are not exposed to public or shared networks such as the Internet.
Administration is simplified.
Using versatile VPN software features, it is simple to add new users or groups of users to networks. So this is great news for businesses that are growing faster than their finances, since it signifies you can often expand network footprints without adding elements or establishing complex network configurations.
Are there any disadvantages to utilizing VPNs?
The success of a VPN is dependent on other components of your network infrastructure. Here are some of the things that might affect your VPN’s performance:
Security concerns associated with configuration
A VPN’s design and installation might be difficult. If you’re unsure how to keep it safe, try hiring an expert network security specialist to ensure VPN security hasn’t been hacked.
Reliability
Because VPN connections rely on the Internet, you must select an Internet service provider (ISP) that regularly provides quality service with little to no downtime.
Scalability
If you need to add additional infrastructure or build new settings, you may encounter technical issues due to incompatibility—especially if you’re integrating goods from various suppliers.
Connection speeds are slow.
If you use a VPN app that offers free VPN service, your connection speed may be poor because these providers do not often provide high-speed connections. Consider whether the speed is enough for your business’s demands.
Should you build your own VPN or purchase one?
Instead of attempting to construct one from scratch, you may purchase a pre-built VPN service. When looking for VPN solutions, inquire about the convenience of configuration.
Setup Instructions for a VPN
How to Setting up a VPN in 6 Easy Steps
Step 1: Arrange main VPN components
You’ll need a VPN client, a VPN server, and a VPN router to be got started. The downloaded client links you to servers all over the world, allowing employees from all over the world to connect to your small company network. Even if workers are utilizing public Wi-Fi networks, the client may be utilized on devices such as cellphones and laptops.
A VPN router is also required to protect and encrypt all network traffic. VPN users are built into a large number of routers.
Step 2: Prepare the devices
VPN clients can occasionally clash with other clients or fail to function correctly. It’s a good idea to prepare your network system before setting up a VPN to avoid complications later on.
As a first step, remove any current VPN client software that you no longer require. In principle, the VPN clients should be able to communicate properly with one another, but rival clients can also be a cause of issues, so it’s better to delete them. This is also an excellent moment to think about network settings. If you intend to set up a VPN for employees who will access online resources over many channels, such as Wi-Fi, 4G modems, and wired connections, you may need to spend more time setting the VPN client. Unplugging unneeded devices from networks might assist to simplify them.
Step 3: Download and install VPN software.
Installing clients from your VPN provider is the simplest method to get your VPN up and running. They may not, however, provide software for every platform you require, such as Windows, iOS, and Android. Although if they wouldn’t, it’s a good idea to run whatever they supply first just double check that your VPN account is active.
Look for the “downloads” tab on the website of your VPN provider. You should also download applications for your employees’ mobile devices, since you’ll want to safeguard connections from as many devices as feasible. If the first client you install works straight away, you may contact the VPN provider to inquire about clients for additional systems. If you are unable to log in at all, you can report this to the VPN provider’s support team.
Step 4: Locate a setup tutorial.
If your VPN provider does not provide software for the devices your company employs, visit the supplier’s website for manual setup instructions. Hopefully, you’ll be able to discover the documents you require. If you don’t, look for setup manuals for similar devices from other providers.
For example, if your company employs Chromebooks, you might look for tutorials tailored to these devices.
Step 5: Login to the VPN.
After you’ve installed the VPN client applications, you’ll need to input your login details. In most cases, the username and password will be the ones you used when you joined up with the VPN service, while some organizations may need you to create a different login for the VPN client.
When you log in, the VPN software normally connects to the server that is closest to your current location.
Step 6: Select VPN protocols
VPN protocols govern how data is sent between your computer and the VPN server. Some protocols aid in speed, while others aid in data privacy and security.
OpenVPN
Because this is an open-source protocol, you may inspect its source code. OpenVPN is quickly becoming an industry standard as well.
L2TP/IPSec
Another well-known protocol is the Layer 2 Tunnel Protocol. It has robust security safeguards and is frequently packaged with the IPSec protocol, which authenticates and encrypts data packets delivered over the VPN.
SSTP
The Microsoft operating system fully supports the Secure Socket Tunneling Protocol.
PPTP
One of oldest Vpns is the Point-to-Point Tunneling Protocol. However, it is becoming less used as faster and more secure protocols become available.
Step 7: Perform troubleshooting
Typically, your VPN provider’s client will begin operating immediately. However, if that is not the case, attempt the following steps:
- Close and reopen the client, and then reset your device.
- If you have any other VPN software active, ensure sure you’re unplugged before shutting it off.
VPN clients require the proper software drivers to function properly. In rare circumstances, you can reinstall programs by selecting the “repair” option. To see if this feature is accessible, go to the options page. Check your login credentials if you’re having problems logging in. Some VPN clients generate their own logins, while others allow you to create your own.
Check that you’re using the right login, and read any welcome emails or quick-start guidelines you may have gotten from the provider if required.
You might also try changing servers. Select a different server that is near to your actual location.
What about Free VPN Services?
Free VPNs that are worth using are hard to come by, but they do exist. Many VPN providers include a free trial period, although this is generally for a limited duration. Others, such as TunnelBear and Hotspot Shield, provide completely free versions but reserve some functionality for premium subscribers. Unfortunately, most VPNs are not free, but you don’t have to break the bank to be safe. After using a service for a month or two, you may save even more money by signing up for a longer-term contract. If you’re on a budget, our list of inexpensive VPNs is a wonderful place to start.